Google stops indexing pages when Cloudflare blocks Googlebot. Your rankings drop because Google cannot crawl, render, or fetch key assets. You can fix this fast if you identify the exact Cloudflare feature that triggers the block, then add a safe allow rule for verified Googlebot, and then confirm the fix in logs and Google Search Console.
Key Takeaways
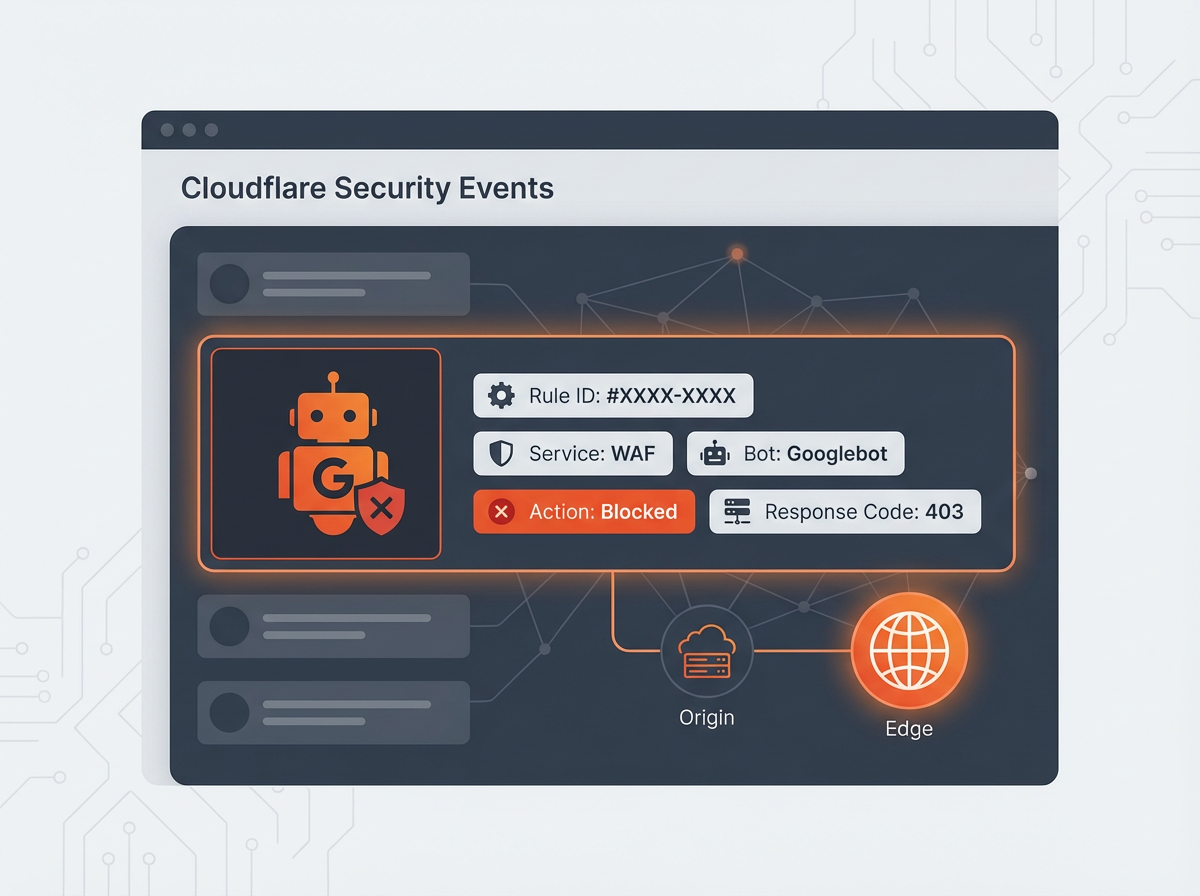
- Find the exact block source first by using Cloudflare Security Events and matching the request to a rule ID.
- Verify real Googlebot before you allow it by using reverse DNS and forward DNS checks.
- Fix common causes by adjusting WAF Managed Rules, custom Firewall rules, and Bot Management settings.
- Disable or tune Bot Fight Mode if it blocks verified bots or creates false positives.
- Allow Googlebot with narrow rules (ASN, verified bot, URI scope) instead of wide IP whitelists.
- Validate the fix with Crawl Stats, URL Inspection, and Cloudflare logs to confirm 200 responses for Googlebot.
Understand why Cloudflare blocks Googlebot
Cloudflare blocks Googlebot when a security control treats the request as suspicious. The most common triggers are WAF Managed Rules, Bot Management signals, rate limiting, and custom Firewall rules. You need to map the block to the product that fired the action. That step prevents guesswork and prevents you from weakening security.
Common block symptoms you will see
- Google Search Console shows Blocked due to access forbidden (403) or Blocked due to other 4xx issue.
- URL Inspection shows Crawl allowed? Yes but Page fetch failed.
- Cloudflare returns 1020 Access Denied (often a Firewall rule) or 403 (often WAF/Bot).
- Google cannot fetch CSS/JS, so rendering fails and indexing quality drops.
Does Cloudflare block bots?
Yes. Cloudflare blocks bots by design when you enable WAF rules, Bot Management, Bot Fight Mode, Super Bot Fight Mode, rate limiting, or strict custom Firewall rules. Cloudflare also allows many verified bots automatically, but misconfigurations and aggressive rules can still block Googlebot.
Next, you need proof of what blocked the request.
Step 1: Confirm the block and identify the exact rule
You fix Cloudflare blocking only after you identify the blocking control. Use Cloudflare Security Events first. Then confirm with logs if you have them.
Use Cloudflare Security Events to find the rule
- Open your Cloudflare dashboard.
- Select your site.
- Go to Security → Overview → Bot traffic → View bot events

- Filter by Action: Block (and also check Managed Challenge if Googlebot gets challenged).

- Filter by User Agent contains Googlebot.

- Click an event and note:
- Service (WAF, Firewall rules, Bot, Rate limiting)
- Rule ID / Rule name
- Host, URI, Country, ASN
- Response code (403, 1020)
Goal: You want one clear answer like “WAF Managed Rules: Cloudflare Specials” or “Firewall rule: Block bad bots” or “Bot Fight Mode.”
Alternatively Go to AI Crawl Control and search for Googlebot from the list and click on three dots icon on last column and click on View metrics;

Here you will find allowed requests and blocked requests;

Check Google Search Console for the exact URL and time
- Open Google Search Console → Pages report.
- Open a blocked example URL.
- Check the last crawl time and the crawl result.
- Run URL Inspection → Test Live URL.
Match the timestamp with Cloudflare events. That match helps you avoid chasing unrelated blocks.
Use Cloudflare logs if available (best proof)
- If you use Logpush, query for the blocked request by URI and user agent.
- Look for fields like ClientRequestUserAgent, EdgeResponseStatus, WAFAction, FirewallMatchesActions, and FirewallMatchesRuleIDs.
Now you know what caused the block. Next, confirm the crawler is real Googlebot.
Step 2: Verify that the request is real Googlebot (avoid spoofing)
Attackers often spoof the Googlebot user agent. If you allow by user agent alone, you can open your site to scraping and attacks. Google provides a verification method based on DNS. Use it before you whitelist a Google bot.
How to verify Googlebot with reverse DNS and forward DNS
- Get the IP address from Cloudflare Security Events or logs.
- Run a reverse DNS lookup (PTR) for the IP.
- Confirm the hostname ends with .googlebot.com or .google.com.
- Run a forward DNS lookup (A/AAAA) for that hostname.
- Confirm the forward lookup returns the same IP address.
Example commands:
host 66.249.66.1(reverse lookup)host crawl-66-249-66-1.googlebot.com(forward lookup)
If the DNS checks fail, do not allow the request as Googlebot. Fix the block only for verified Googlebot.
Next, apply the right fix based on the product that blocked the request.
Fix 1: Firewall rules that block Googlebot (custom rules and IP rules)

Custom Firewall rules often cause 1020 errors. These rules can block by country, ASN, path, threat score, user agent, or a bot score. You need to find the rule and then add an allow exception above it.
How to fix Cloudflare blocking from a Firewall rule
- Go to Security → Security rules (or Security → Firewall rules depending on your plan/UI).

- Find the rule ID from Security Events.
- Open the rule and review the expression.
- Check for conditions like:
(http.user_agent contains "bot")(cf.threat_score > 10)(ip.geoip.country in {"CN" "RU"})with broad blocks(cf.client.bot)
Add a safe allow rule for verified bots
Use Cloudflare’s verified bot signals when available. Prefer a rule that allows verified Googlebot traffic and keeps other bots filtered.
- Create a new rule at the top with action Allow.
- Use one of these strategies (use what your account supports):
- Allow Verified Bots if Cloudflare exposes a verified bot field in your plan/UI.
- Allow by ASN 15169 (Google) plus a narrow URI scope.
- Allow by IP list only if you maintain it and you also verify DNS (least preferred).
Practical allow rule patterns (choose one):
- Option A (best if available): Allow if request is from a verified bot category and matches Google.
- Option B (often available): Allow if
ip.geoip.asnum eq 15169andhttp.request.uri.pathmatches crawl paths you need.
Important: Do not allow by user agent alone. Do not disable your blocking rule if it protects sensitive endpoints.
After you fix custom rules, check WAF Managed Rules. Many sites get blocked there.
Fix 2: WAF Managed Rules blocking Googlebot (Cloudflare Specials and OWASP)
WAF Managed Rules can block Googlebot if the crawler hits URLs that look like attacks. This happens often on search pages, filter pages, and URLs with many query parameters. You should tune the exact rule that fired. You should not disable the full WAF unless you have no other choice.
Find the Managed Rule that triggered the block
- Go to Security → Security rules.
- Use the rule ID from Security Events to locate the exact rule set and rule.
- Check the action: Block, Challenge, or Log.
Fix “Cloudflare Managed Special rules are blocking Googlebot”
- Open the Cloudflare Managed Rules section.
- Locate Cloudflare Specials (name can vary by UI version).
- Do one of the following:
- Set the specific rule to Log for Googlebot requests.
- Create an exception that skips the rule for verified Googlebot.
- Disable only the single rule that causes false positives on safe URLs.
Create a WAF exception for Googlebot on safe paths
Use exceptions to keep protection for users while letting Google crawl.
- Scope the exception to:
- Verified Googlebot traffic (preferred)
- Or Google ASN 15169 plus DNS verification process
- Scope the exception to:
- Public pages only (for example:
/blog/,/products/) - Exclude admin paths (for example:
/wp-admin,/login)
- Public pages only (for example:
- Keep a log-only period first if you are unsure.
Fix OWASP false positives without weakening security
- If OWASP rules block URLs with many parameters, reduce the sensitivity for that rule group.
- If a specific parameter triggers SQLi or XSS rules, add a targeted exception for that parameter on that endpoint.
- Keep blocking enabled for login, checkout, and API endpoints.
Next, check Bot Management. It can block Googlebot even if WAF looks fine.
Fix 3: Bot Management and Bot Fight Mode blocking Googlebot
Bot controls can block or challenge crawlers based on behavior signals. If your configuration treats automated traffic as hostile, Googlebot can get blocked. You should allow verified bots and reduce aggressive actions on crawl traffic.
How to disable Bot Fight Mode in Cloudflare
- Open Cloudflare dashboard and select your site.
- Go to Security → Bots (menu name can vary).
- Find Bot Fight Mode or Super Bot Fight Mode.
- Toggle it Off or switch to a less aggressive mode.
- Save changes and retest in Search Console.
Safer alternative: keep Bot Fight Mode, but allow verified bots
- Enable settings that allow Verified Bots if available.
- Create a custom rule that skips bot checks for verified Googlebot on public paths.
- Keep bot protections on high-risk paths like
/wp-login.php,/cart, and/api.
Fix Bot Management blocks caused by score thresholds
- Review actions tied to bot score or bot categories.
- Change action from Block to Managed Challenge for general traffic if you see false positives.
- Add an allow exception for verified Googlebot so it never gets challenged.
After Bot settings, review rate limiting. Rate limits can block crawlers on large sites.
Fix 4: Rate limiting and crawl bursts that trigger blocks
Googlebot can crawl fast after site changes. A strict rate limit can block it. You should tune rate limits to protect login and API endpoints while allowing crawl traffic on public pages.
How to check if rate limiting blocks Googlebot
- In Security Events, look for a service label that points to Rate limiting.
- Check if blocked requests cluster in a short time window.
- Check if the URI is a public page list or a sitemap fetch.
How to fix rate limiting without removing protection
- Increase thresholds for public GET requests.
- Keep strict thresholds for POST requests and authentication endpoints.
- Add an allow rule for verified Googlebot on:
/sitemap.xml/robots.txt- Key category and product pages
Next, confirm that SSL/TLS and firewall settings do not create crawl failures.
Fix 5: SSL/TLS, redirects, and edge settings that look like blocking
Some crawl failures look like blocking but come from redirect loops, TLS errors, or blocked resources. Googlebot needs consistent 200 responses and stable redirects.
Check for redirect loops and mixed schemes
- Test the URL with and without
www. - Test
httpandhttpsversions. - Confirm you have a single canonical redirect path.
Check Cloudflare SSL mode
- Go to SSL/TLS → Overview.
- Use Full (strict) if your origin has a valid certificate.
- Avoid Flexible if it causes redirect loops at the origin.
Check robots.txt and origin firewall rules
- Confirm
/robots.txtreturns 200 and does not disallow important paths. - Confirm your origin firewall (server, CDN, load balancer) does not block Google IPs.
- Confirm your hosting WAF does not block Googlebot while Cloudflare allows it.
Now you can whitelist Googlebot safely with a clean rule design.
How to whitelist a Google bot safely (recommended rule design)
A safe whitelist uses verification signals and narrow scope. A risky whitelist uses only a user agent match or a broad IP allow. Use the safe approach so you keep protection for real attacks.
Rule design checklist (use this before you click “Allow”)
- Use verified bot detection if your plan supports it.
- Use DNS verification for any suspicious case.
- Scope the allow to public content paths only.
- Do not allow access to admin, login, or private API endpoints.
- Place the allow rule above block rules that catch bots.
- Log the allowed traffic for a week and review anomalies.
Example allow scopes that work well
- Allow Googlebot to crawl content: public GET requests to
/,/blog/,/category/,/product/. - Allow Googlebot to fetch assets:
/wp-content/,/static/,/assets/. - Always allow:
/robots.txtand/sitemap.xml.
What to avoid when you whitelist Googlebot
- Do not create a rule like
http.user_agent contains "Googlebot"with action Allow. - Do not disable the full WAF rule set to solve one false positive.
- Do not allow all of ASN 15169 to all endpoints if you run sensitive APIs.
Next, validate the fix with a repeatable test plan.

Validate the fix (prove Googlebot can crawl and index)
You need confirmation from both Cloudflare and Google. Use a short test loop. Then watch crawl data for several days.
Validation checklist in Cloudflare
- Open Security Events and confirm no new blocks for Googlebot user agents.
- Confirm the action for Googlebot requests is Allow or Skip for the correct feature.
- Confirm response status is 200 for key URLs.
Validation checklist in Google Search Console
- Run URL Inspection → Test Live URL on a previously blocked page.
- Click View tested page and confirm resources load.
- Request indexing for a small set of important pages.
- Monitor Crawl stats for drops in 4xx responses.
Validation checklist on your origin
- Check origin access logs for Googlebot requests that reach the server.
- Confirm your origin security tools do not block the same IPs.
Next, prevent the issue from returning with a simple monitoring routine.
Prevent future Googlebot blocks (monitoring and safe defaults)
Most repeat incidents happen after a rule change. You can prevent them by keeping a small set of guardrails and by logging bot-related actions.
Set safe defaults for WAF and bot controls
- Keep WAF enabled, but tune false positives with exceptions.
- Keep bot protection enabled for login and API endpoints.
- Use Log mode first for new managed rules if your site has many query URLs.
Change control checklist for Cloudflare security edits
- Record the rule change and the reason.
- Test with a staging hostname if you have one.
- After deployment, check Security Events for Googlebot within 30 minutes.
- Re-test 5 to 10 key URLs in Search Console within 24 hours.
Keep a “crawl allow” policy that stays narrow
- Allow verified Googlebot on public content paths.
- Keep challenges for unknown bots.
- Keep strict rules for admin and payment paths.
Frequently Asked Questions (FAQs)
How to fix Cloudflare blocking?
Open Cloudflare Security Events, find the blocked request, note the rule ID and service, then tune or add an allow exception for verified Googlebot. Retest in Google Search Console.
How do I whitelist a Google bot?
Verify the crawler with reverse DNS and forward DNS, then create an allow rule based on verified bot signals or Google ASN with a narrow path scope. Do not allow by user agent alone.
Does Cloudflare block bots?
Yes. WAF rules, Bot Management, Bot Fight Mode, and rate limits can block or challenge bots. Bad configuration can also block good bots like Googlebot.
How to disable bot fight mode in Cloudflare?
Go to your site in Cloudflare, open Security → Bots, find Bot Fight Mode (or Super Bot Fight Mode), toggle it off, save, and then retest crawl in Search Console.
Why does Google Search Console show 403 but I can load the page?
Cloudflare can block specific user agents or IP ranges while allowing browsers. Googlebot can also fetch assets and parameters that you do not test in a normal browser session.
Should I turn off Cloudflare WAF to let Googlebot crawl?
No. Turn off only the specific rule that causes false positives, or add a targeted exception for verified Googlebot on public paths. Keep WAF protection for sensitive endpoints.
Final Thoughts
How to Fix Googlebot Blocking in Cloudflare (Firewall, Bot Management, WAF Rules) comes down to one workflow: identify the exact blocking feature in Security Events, verify real Googlebot with DNS checks, apply a narrow allow or exception rule, and then confirm the result in Search Console and logs. If you want a fast win, start by locating the rule ID that fired, then tune Managed Rules or Bot settings instead of disabling security. If you need help, export a blocked event from Cloudflare and share the rule ID with your team so you can fix the exact control without weakening your site.
Test your knowledge
Take a quick 5-question quiz based on this page.