Phishing is a form of fraud where an attacker creates a website that looks like the one you are trying to visit. They then trick you into entering your username and password on the fake site. In this Tutorial We will learn Do you want to know How to protect against phishing attacks.
Once they have your information, they can log into your account and do whatever they want with it. The key is to avoid clicking on a fraudulent link in an email or online. Phishing attacks fool people because attackers go to great lengths to make them look like legitimate messages.
Also Read: What is an IDOR Vulnerability? How to prevent it
Unfortunately, scammers are getting more sophisticated with how they attack, so your guard must be up all the time. Let’s look at some steps you can take to avoid becoming the victim of a phishing attack and how to prevent phishing.
More than 80% of security incidents are caused by phishing assaults. According to the CISCO 2021 Cybersecurity Threat Trends report, phishing is responsible for about 90% of data breaches. Spear phishing is the most prevalent form of phishing assault, with 65 percent of all phishing operations.
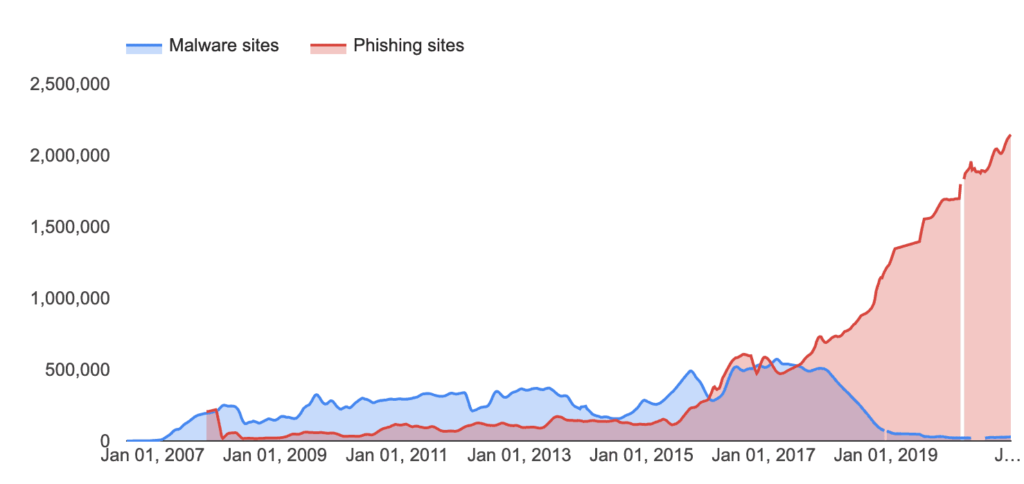
Here are some recent events happened with Phishing attacks;
In Q1 2024, Microsoft and Google topped the list of the most imitated brands in phishing attacks, constituting 38% and 11% of all brand phishing attempts, respectively. Notably, Airbnb made its debut in the top 10, likely due to heightened visibility during the Easter travel season (Check Point Research).
Phishing attacks targeting CEO and CXO-level executives—known as whaling or CEO fraud—have surged 2-3 times over the past year. Organized criminal gangs are leveraging AI and social engineering to impersonate executives, tricking employees into divulging sensitive data or transferring money (Economic Times).
In May 2024, a significant phishing campaign targeted North American university students and staff with a “free piano” bait, netting the attackers at least $900,000 (CM Alliance).
Additionally, AT&T’s email servers blocked connections from Microsoft 365 in May 2024 due to a surge in spam originating from Microsoft’s service (CM Alliance).
Also in May 2024, the American Radio Relay League (ARRL) experienced a cyberattack that disrupted its IT systems and online operations, including the Logbook of the World (CM Alliance).
Phishing attacks increased by 58.2% in 2023 compared to the previous year. The rise of voice phishing (vishing) and deepfake phishing attacks highlights how attackers are employing AI tools. Furthermore, adversary-in-the-middle (AiTM) and browser-in-the-browser (BiTB) phishing attacks are becoming significant threats (Zscaler).
In Q2 2024, the Anti-Phishing Working Group (APWG) reported a total of 877,536 phishing attacks, with increasing use of phone calls and text messages to target bank and payment service customers (APWG).
Understanding Phishing
Definition and Explanation of Phishing
Phishing is a type of cybercrime where scammers send fraudulent emails, messages, or phone calls to trick victims into revealing sensitive information, such as personal or financial information. The goal of phishing is to obtain this information to commit identity theft, financial fraud, or other malicious activities. Phishing scams can occur through various channels, including email, phone calls, text messages, and even social media.
How Phishing Works and Its Goals
Phishing works by creating a sense of urgency or trust with the victim, often by pretending to be a legitimate company or institution. The scammer may use various tactics, such as vishing (voice phishing), smishing (SMS phishing), or whaling (targeting high-level executives), to trick the victim into revealing sensitive information. The goals of phishing include obtaining personal identifying information, such as account passwords, Social Security numbers, or credit card information, to commit identity theft or financial fraud.
Who is at Risk of Phishing Attacks?
Anyone who uses the internet, phone, or text messages can be a target for phishing scammers. Phishing attacks can affect individuals, businesses, and organizations of all sizes. The risk of phishing attacks is higher for those who use public Wi-Fi networks, click on suspicious links or attachments, or respond to unsolicited phone calls or text messages.
Types of Phishing Scams
There are several types of phishing scams, including:
- Email Phishing: Scammers send fraudulent emails that appear to be from a legitimate company or institution.
- Phone Phishing: Scammers make phone calls to trick victims into revealing sensitive information.
- Text Message Phishing: Scammers send text messages that appear to be from a legitimate company or institution.
- Whaling: Scammers target high-level executives or individuals with access to sensitive information.
- Vishing: Scammers use voice phishing to trick victims into revealing sensitive information.
- Smishing: Scammers use SMS phishing to trick victims into revealing sensitive information.
To protect yourself from phishing attacks, it’s essential to be aware of these tactics and take steps to prevent phishing, such as using strong passwords, enabling two-factor authentication, and being cautious of unsolicited phone calls or text messages.
How to Protect Against Phishing Attacks
Now that you know the different types of phishing attacks, let’s look at how to prevent phishing attacks with some steps you can take to protect yourself:
- Never click on a link in an email or online unless you’re absolutely sure it’s legitimate. If you’re not sure, go to the website directly by typing the URL into your browser.
- If you receive an email from a company or organization you’re not familiar with, do some research before clicking on any links. You can usually find reviews of the company online.
- Never give out personal information or login credentials over the phone unless you’re absolutely sure you’re talking to a legitimate representative.
- Keep your antivirus and anti-malware software up to date. These programs can help to protect your computer from malicious software.
- Be careful of any attachments you receive in emails, even if they’re from people you know. If you’re not expecting an attachment, it’s best to delete the email.
- Keep your operating system and browser up to date with the latest security patches.
By following these steps, you can protect against phishing attacks but to give you detailed output we have outlined some measures which you can adopt to protect against phishing attacks.
Use a password manager

A password manager is an application that creates, stores and retrieves passwords for you so you don’t have to. It is crucial for maintaining the security of your online accounts by ensuring that your passwords are strong and unique. There are a few reasons why these are helpful:
When you’re on a website and ready to submit your username and password, the browser checks with the password manager to make sure the site is legitimate. The browser sends a hash of the URL (that’s basically a unique identifier of that web page), and the password manager checks its database to see if it has any record of this URL.
If there is no match (i.e., you’ve never saved login information for this domain), then the password manager pops up a warning saying this is not a recognized site, and your login information will not be filled in automatically.
This simple check can stop many phishing attacks from succeeding because it prevents users from entering their usernames and passwords on suspicious sites without extra confirmation.
Of course, for this to work effectively, you need to use your password manager regularly — particularly when logging into new websites, such as online stores or forums where you’ve never had an account before. Another advantage of using a password manager: you’ll never forget or lose your passwords again!
Don’t open emails or click on links from anyone you don’t trust

Don’t open emails or click links sent by anyone you don’t know and trust, as they could be part of a phishing scam. The best way to avoid phishing attacks is to ignore hyperlinks or attachments in emails sent by people you don’t know, no matter how intriguing they seem.
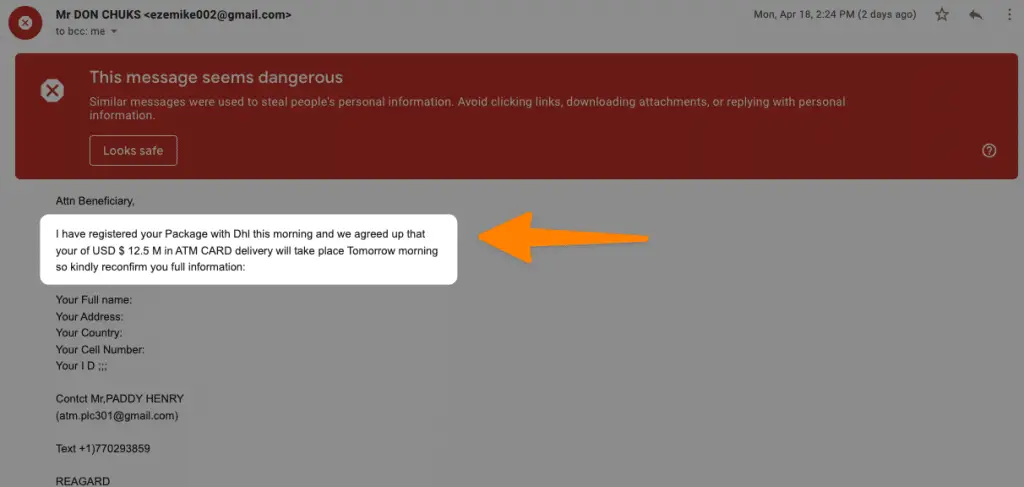
If you are unsure whether an email is a phishing attack, there are ways to confirm its legitimacy immediately. If the sender appears to be someone you know but you haven’t received other correspondence from them recently, don’t trust it. Instead, call him/her and ask first before clicking anything.
For example: if your mom emailed you a link without giving any explanation other than “click here” or with the subject line “Hey!”, that should be a red flag — she would normally write something more detailed than that (especially if she doesn’t email very often).
Be careful with phishing emails you do trust (even from friends)

You’ve probably heard about the dangers of phishing emails, but you may be less aware of the risks posed by a compromised account.
Even if you trust the sender, their email could have been hacked and used to send malicious code to your inbox.
It’s important to be careful with any email you receive — even from someone who is usually reliable.
If you receive an email that seems suspicious, consider these warning signs:
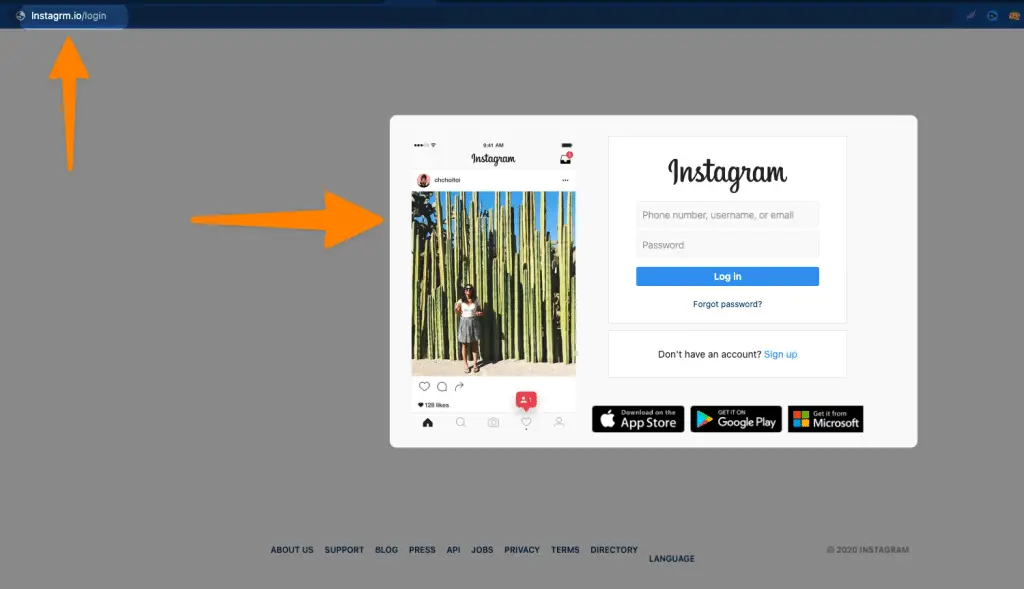
These kinds of templates are available for free on github which is the largest code repositery.
• The sender’s email address doesn’t match what it should be. For example, it could use “I” instead of “L.”
• The message includes suspicious attachments or links that are difficult to read or unrecognizable (they shouldn’t look legitimate).
• The content doesn’t seem like something the person would normally send. Or maybe there is content missing (like a signature) where there should be content.
• There was no introduction at all and no mention of why they’re contacting you. This can also apply to messages with generic language like “Dear customer” or “Valued client.”
• There is urgency in the subject line and/or body of the message that raises suspicions (e.g., “Take action now” or “Act quickly”).
Search for trusted versions of apps and websites

Make sure you have the real version of any app you download and are visiting the official website. Otherwise, a fake version could be used to steal your account details or lead you to phishing sites.
For apps, make sure you only download them from official app stores, like Google Play for Android or the App Store for iOS.
When using websites, check for a green padlock next to the URL in your browser’s address bar.
This shows the website is secure, and it’s less likely that someone could tamper with it to get your account details.
If there is no padlock when you sign in to an account or enter personal information on an unfamiliar website, it’s best not to proceed any further until one appears.
When it comes to phishing attacks or sites that look like they’re part of your bank but are trying to steal your personal information, be cautious. These types of sites can take one of two routes.
Either they’ll try to trick you into giving out more information than you should (by pretending to be a bank), or they’ll use misspelt words and numbers in their URL (so the URL looks similar but has errors).
When in doubt, go directly to the site or app yourself through your browser

If you think an email might be a phishing attack, don’t click on any links. Instead, open your browser and manually go to the website or app.
Then log in. It’s really that easy: if you’re being phished, the website or app won’t recognize you as a user, but if it’s real, you can log in without any problems.
This way, you can be sure the website or app is legitimate, and you’re not giving away your account details to a hacker.
Be aware of phishing attacks that target your phone for sensitive information

Phishing isn’t just something that happens on your computer. Hackers can also target your mobile phone with text messages (SMS) or calls.
This type of phishing is known as “SMiShing” or “fishing like.” Just with email phishing, these attacks can come from fake websites or apps.
They can also come from seemingly legitimate companies, pretending to be customer service or asking you to update your account details.
Again, the best way to protect yourself is to be aware of the risks and know what to look for to prevent phishing attacks.
If you get a text message or call from someone you don’t know, be wary.
Don’t click on any links or give out any personal information until you’ve verified that the request is legitimate.
You can do this by searching for the company’s customer service number online and calling them directly.
Never give out your personal information to someone you don’t know, even if they say they’re from a legitimate company.
If you think you might have fallen for a phishing attack, act quickly

If you think you might have given away your account details to a hacker, it’s important to act quickly.
First, change your password and enable two-factor authentication (if it’s an option).
This will help to protect your account from being accessed by someone else.
Then, you should contact the company whose account you think has been compromised.
Phishing attacks are dangerous and hard to spot, but you can take steps to avoid them by being careful about where you grant access in your online life.
Phishing attacks are a serious problem, and it can be hard to spot them. The best way to avoid being a victim is to be careful about where you grant access in your online life.
Phishing attacks are common — the attacker tries to bait you into giving them access to an account or providing personal information. Be aware and take these precautions.
What to do after a phishing attack
If you think you may have fallen for a phishing attack, there are a few things you should do:
- Change your password on the site that was attacked, and any other sites where you use the same password.
- Be wary of any emails, messages, or calls from someone claiming to be from the company that was attacked, even if they seem to have legitimate information. Scammers may try to exploit the situation by impersonating company representatives.
- Keep an eye out for any strange activity on your account, such as new charges or unusual login activity.
If you have any concerns that your personal information may have been compromised in a phishing attack, you should contact your bank or credit card provider immediately. You may also want to consider signing up for a credit monitoring service to help protect your identity in the future.
How to respond to a phishing attack
If you receive a phishing email, message, or call, do not respond to it. If you think the communication may be legitimate, contact the company directly using a phone number or email address you know to be real. Do not use any contact information provided in the suspicious communication.
If you clicked on a link in a phishing email or provided personal information to a phishing website, take steps to secure your account:
- Change your passwords on any accounts that may have been compromised. Choose strong passwords that are difficult to guess.
- Enable two-factor authentication, if available. This adds an extra layer of security by requiring you to enter a code from your phone in addition to your password when logging in.
- Keep an eye out for any strange activity on your accounts, such as new charges or unusual login activity.
If you are concerned that your personal information may have been compromised, you should consider signing up for a credit monitoring service. This can help protect your identity in the future by alerting you to changes in your credit report.
How do spear-phishing attacks differ from standard phishing attacks?
Spear-phishing attacks are targeted phishing attacks that are designed to trick a specific individual or organization into giving up sensitive information.
Standard phishing attacks, on the other hand, are mass emails that are sent out to a large number of people in the hopes that someone will take the bait.
While both types of phishing attacks can be devastating, spear-phishing attacks are often more successful because they appear to come from a trusted source.
What makes phishing attacks so easy to fall for?
There are a few reasons why phishing attacks can be so convincing:
- The attacker may spoof the email address or website of a trusted company or individual.
- The attacker may create an email or website that looks very similar to a legitimate one.
- The attacker may use social engineering techniques to trick you into thinking the communication is legitimate.
how many businesses are targeted by spear-phishing attacks each day?
It is difficult to say how many businesses are targeted by spear-phishing attacks each day, as many of these attacks go unreported. However, it is estimated that over 90% of all cyberattacks begin with phishing emails.
Spear-phishing attacks are often more successful than standard phishing attacks because they appear to come from a trusted source. This makes them difficult to detect and can cause serious damage to businesses if they are not prepared.
Businesses can protect themselves against spear-phishing attacks by implementing security measures such as two-factor authentication and training employees to recognize phishing emails.